Resources - Our Platform Documentation
In the complex realm of cybersecurity, traditional agent-based solutions often add more complexity than clarity. RedRok’s agentless DeepScan technology, rooted in ethical hacking, offers a proactive approach to cybersecurity by continuously identifying and managing threats without the need for endpoint software installations. This innovative method provides real-time visibility across entire digital environments, uncovering vulnerabilities, validating security controls, and ensuring comprehensive coverage, including unmanaged and IoT devices, thereby shifting security teams from a reactive to a proactive defense posture.
Continuous Threat Exposure Management (CTEM) represents a proactive shift in cybersecurity, emphasizing ongoing identification and management of security exposures across digital infrastructures. Unlike traditional reactive measures, CTEM employs an ethical hacker's mindset to continuously uncover hidden attack vectors, ensuring real-time resilience against threats. RedRok's DeepScan technology enhances this approach with agentless operation, providing comprehensive visibility without performance degradation, thereby transforming security teams from reactive to proactive defenders.
Supply chain attacks are a significant risk as attackers exploit third-party vulnerabilities to infiltrate target organizations. Traditional security tools often lack visibility into these external dependencies. RedRok's Continuous Threat Exposure Management (CTEM), featuring DeepScan technology, proactively addresses these challenges by simulating attacker techniques without needing agents. This approach uncovers hidden vulnerabilities and validates security controls, offering comprehensive, real-time insights critical for defending against supply chain threats.
Continuous Threat Exposure Management (CTEM) is gaining traction as traditional security tools struggle with the complexities of modern IT environments. CTEM, implemented through solutions like RedRok's agentless DeepScan, focuses on proactive, adversary-centric approaches to identify and prioritize potential vulnerabilities before they can be exploited. This approach not only enhances security posture by continuously validating controls but also alleviates alert fatigue by offering actionable insights, thereby improving efficiency and compliance.
The increasing threat of cyberattacks on critical infrastructure demands a shift from traditional security measures to proactive solutions like RedRok’s agentless DeepScan. By continuously identifying and prioritizing vulnerabilities from an attacker’s perspective, it offers unparalleled visibility without disrupting operations, ensuring the resilience of essential systems.
Penetration testing offers a valuable snapshot of digital security at a specific moment but lacks continuous oversight. Continuous Threat Exposure Management (CTEM), enhanced by RedRok's agentless DeepScan technology, provides ongoing assessment of the entire attack surface, identifying vulnerabilities in real time without deployment complexities. CTEM complements traditional testing, ensuring constant vigilance and proactive risk management for evolving digital environments.
The article explores the rapid evolution of the cybersecurity landscape, highlighting the shift from reactive to proactive defenses against increasingly sophisticated cyber threats. It emphasizes the limitations of traditional security tools, such as EDR and XDR, and introduces RedRok's Continuous Threat Exposure Management (CTEM) with its agentless DeepScan technology. CTEM allows for comprehensive, real-time visibility and proactive identification of vulnerabilities and attack paths, offering a strategic advantage in managing digital security risks.
In today's digital operations, a disconnect exists between security and IT teams, with security focusing on threat prevention and IT prioritizing operational efficiency. This gap leads to fragmented defenses and vulnerabilities, often exploited by attackers. Centralized exposure insights, like those provided by RedRok's DeepScan, offer a unified approach by aggregating and contextualizing security data across hybrid environments, fostering collaboration and transitioning from reactive measures to proactive defense against complex attack paths.
Traditional cybersecurity methods fall short due to their reactive nature, focusing only on known threats. Attackers exploit blind spots, logical flaws, and poorly monitored segments. A shift to proactive strategies such as Continuous Threat Exposure Management (CTEM) is vital, involving continuously discovering, prioritizing, and addressing vulnerabilities from an adversary’s perspective, as highlighted by RedRok’s agentless DeepScan technology.
Despite heavy investments in security tools, organizations remain vulnerable to cyber threats due to reactive strategies and reliance on legacy tools. Attacker-centric testing and continuous validation, such as RedRok's agentless CTEM and Deepscan technology, offer proactive solutions by simulating real attacker behaviors to identify hidden vulnerabilities and enhance security resilience beyond mere compliance.
Shadow IT represents a growing security threat as unauthorized applications and devices proliferate outside the IT department's watch, creating blind spots for traditional security tools. This unmanaged infrastructure poses risks beyond compliance fines, exposing organizations to data breaches, malware, and significant financial losses. Traditional defenses like EDR and XDR fail against Shadow IT due to their reliance on known asset monitoring. An agentless approach, such as RedRok's Deepscan, offers a solution by continuously uncovering hidden vulnerabilities and providing comprehensive visibility, enabling organizations to proactively manage threats and secure their digital environments.
The modern enterprise landscape is a complex digital ecosystem combining on-premises infrastructure with multiple cloud environments, creating potential security blind spots. Traditional security tools cannot fully address these vulnerabilities. RedRok's agentless DeepScan technology offers continuous, comprehensive visibility and proactive exposure management to secure hybrid environments effectively.
RedRok revolutionizes cybersecurity by shifting from reactive incident response to proactive threat anticipation with its agentless DeepScan technology. Emphasizing an ethical-hacker mindset, it provides continuous visibility and real-time validation across networks, cloud, and unmanaged systems, revealing critical vulnerabilities often missed by traditional tools.
In the high-stakes world of cybersecurity, many organizations rely on traditional perimeter-focused tools, which leave them vulnerable to sophisticated attackers who exploit internal misconfigurations and hidden paths. RedRok's DeepScan shifts focus from reactive detection to proactive Continuous Threat Exposure Management (CTEM), using an agentless approach to continuously map network vulnerabilities from an adversary's perspective. By discovering unseen attack vectors and validating security controls in real-time, DeepScan offers a dynamic, comprehensive defense strategy, closing critical blind spots overlooked by legacy systems.
In the realm of cybersecurity, traditional periodic approaches to threat detection are insufficient for combating modern, dynamic threats. Continuous Threat Exposure Management (CTEM) provides a necessary shift by enabling real-time, comprehensive monitoring and proactive identification of vulnerabilities. RedRok's DeepScan technology exemplifies this approach with its agentless, continuous threat evaluation that delivers actionable insights without adding complexity. Transitioning to CTEM ensures organizations maintain resilient security postures, effectively countering the evolving threat landscape.
The digital landscape is evolving with sophisticated threats, necessitating a shift from traditional EDR, which is reactive and focused on individual endpoints, to Continuous Threat Exposure Management (CTEM). CTEM proactively identifies and remediates vulnerabilities across the entire attack surface, offering comprehensive visibility and reducing the attacker's potential pathways, thus complementing and enhancing existing security measures.
Despite significant investment in security tools, organizations often face vulnerabilities due to fragmented systems that attackers exploit. This disjointed setup creates security blind spots, as traditional tools fail to provide unified visibility. RedRok's DeepScan™ addresses these issues with an agentless approach, offering comprehensive, real-time visibility across an organization's entire attack surface, identifying unseen attack vectors, and validating security controls from an attacker’s perspective.
In the ever-evolving digital threat landscape, traditional reactive cybersecurity methods are falling short as attackers grow more sophisticated. RedRok's continuous threat exposure management (CTEM) and agentless DeepScan™ technology offer a proactive solution by adopting a hacker's mindset to anticipate threats and uncover hidden vulnerabilities before exploitation. This approach provides comprehensive coverage, continuous validation of security controls, and contextual, real-time insights, enabling organizations to shift from reactive to strategic risk management and ensure robust protection across on-premise, cloud, and Active Directory environments.
The digital landscape necessitates a shift from reactive security to proactive Continuous Threat Exposure Management (CTEM), as traditional tools struggle against modern threats. RedRok's agentless DeepScan™ provides comprehensive, real-time exposure insights, moving beyond static, agent-dependent methods. This approach reduces attacker dwell time, optimizes security investments, and enhances compliance by delivering actionable, continuous insights into an organization's vulnerabilities and security efficacy.
RedRok's DeepScan™ offers agentless Continuous Threat Exposure Management (CTEM), providing organizations unprecedented visibility into critical cybersecurity blind spots. It identifies and addresses vulnerabilities in unmanaged assets, misconfigurations, legacy systems, and supply chain links by continuously discovering, validating, and prioritizing security risks without the need for intrusive agents. This proactive approach empowers security teams to anticipate and neutralize threats, turning reactive defense strategies into proactive threat exposure management.
In cybersecurity, traditional tools often miss the unseen threats due to inherent visibility gaps. RedRok's DeepScan, using an agentless approach inspired by ethical hackers, offers continuous threat exposure management by mapping digital footprints and identifying vulnerabilities without relying on agents. This proactive methodology provides actionable insights, validating security controls in real-time to reduce risks before attacks occur.
The cybersecurity industry is shifting from a reactive to a proactive approach, emphasizing anticipation and prevention of attacks through Continuous Threat Exposure Management (CTEM). This new paradigm leverages agentless technology for comprehensive, real-time visibility, and adopts an ethical hacker mindset to identify and mitigate vulnerabilities before they can be exploited, moving beyond traditional detection tools like EDR/XDR.
In the evolving realm of cybersecurity, traditional tools like EDR, XDR, and firewalls often leave critical blind spots, overlooking vulnerabilities within unmanaged devices and intricate internal networks. Continuous Threat Exposure Management (CTEM) offers a proactive solution by mapping and prioritizing attack paths, emphasizing a comprehensive, attacker's perspective for truly resilient security defense.
The cybersecurity industry is shifting from a reactive to a proactive approach, emphasizing anticipation and prevention of attacks through Continuous Threat Exposure Management (CTEM). This new paradigm leverages agentless technology for comprehensive, real-time visibility, and adopts an ethical hacker mindset to identify and mitigate vulnerabilities before they can be exploited, moving beyond traditional detection tools like EDR/XDR.
AI is crucial in modernizing vulnerability management by automating detection and response, prioritizing threats, and maintaining round-the-clock monitoring. It alleviates the burden on human analysts and enhances decision-making, exemplified by AMSEC’s integrated AI-driven platform that ensures robust defenses. As digital threats evolve, AI-driven strategies are vital in maintaining security and resilience.
Innovative agentless technologies like RedRok’s DeepScan™ shift the cybersecurity landscape from traditional, agent-reliant defenses to continuous validation strategies. By eliminating the need for disruptive agents, organizations benefit from real-time security validations and comprehensive threat coverage, enabling proactive threat management and integration with existing systems without operational inefficiencies. Horizon-focused and adaptable, this approach meets the demands of evolving cyber threats.
Agentless security offers a modern approach to cybersecurity by eliminating the need for endpoint software, thus improving system performance, visibility, and threat detection. Technologies like RedRok's DeepScan™ ensure continuous monitoring and real-time validation without burdening devices, making them an essential component for proactive cyber defense.
In the ever-evolving landscape of cybersecurity, traditional Endpoint Detection and Response (EDR) systems often fail to detect sophisticated threats. To address these limitations, Continuous Threat Exposure Management (CTEM) offers a cutting-edge, real-time approach, enabling organizations to continuously validate security defenses, gain actionable insights, and proactively manage exposure by anticipating and preventing threats.
NIS2 at a Glance The EU Network & Information Security Directive (NIS2) toughens the 2016 framework by expanding coveredsectors, mandating continuous risk …
Cybersecurity professionals continually face the critical challenge of timely remediation. The longer vulnerabilities remain unresolved, the greater the risk of exploitation. Yet, …
As threats evolve at unprecedented speed, proactive preparation is paramount. Discover the future cyber landscape and how RedRok empowers your organization to …
The digital landscape is evolving rapidly, with financial institutions and technology service providers at the forefront of innovation—and increasingly exposed to operational …
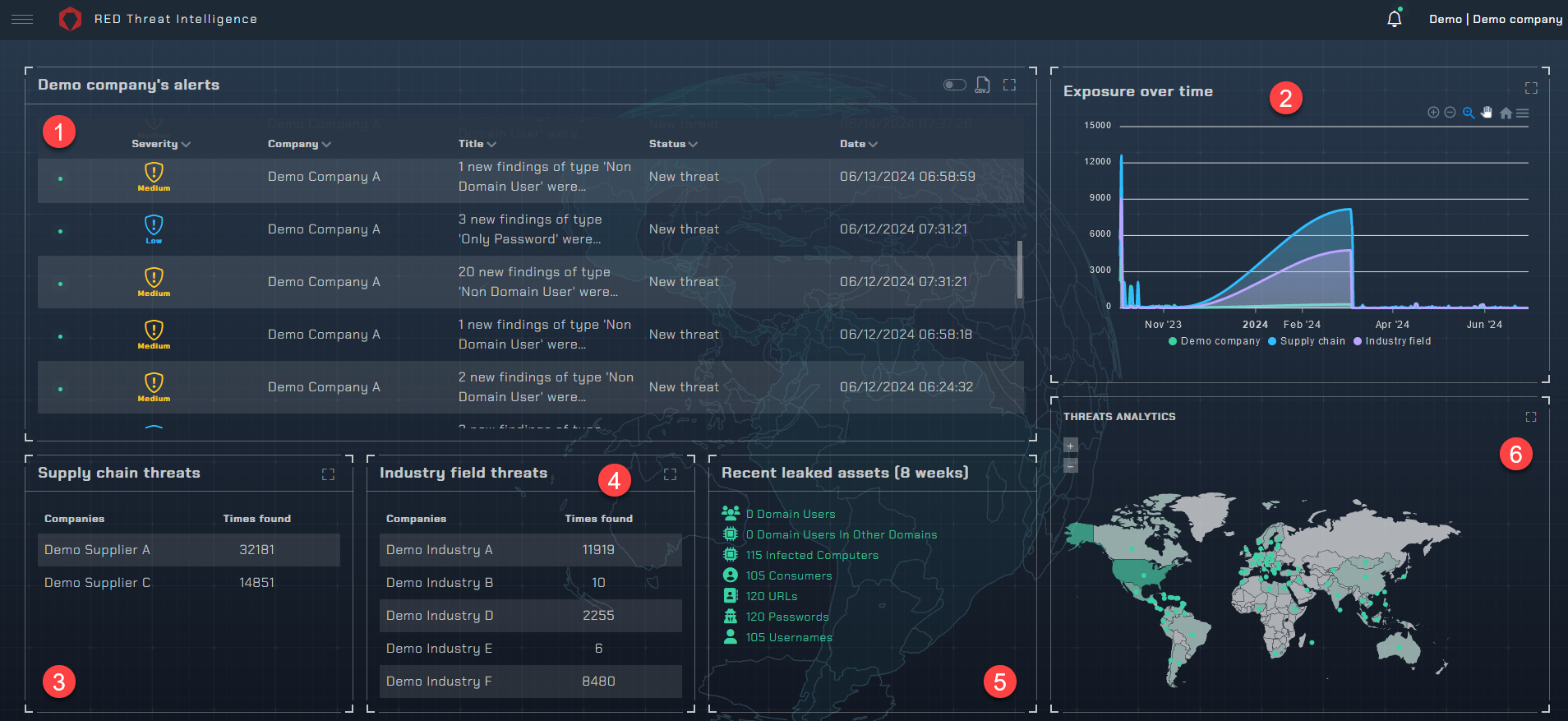
Welcome to the RedRok Intelligence Dashboard! This tutorial will guide you through the interface’s main features of our intelligence platform, ensuring you …
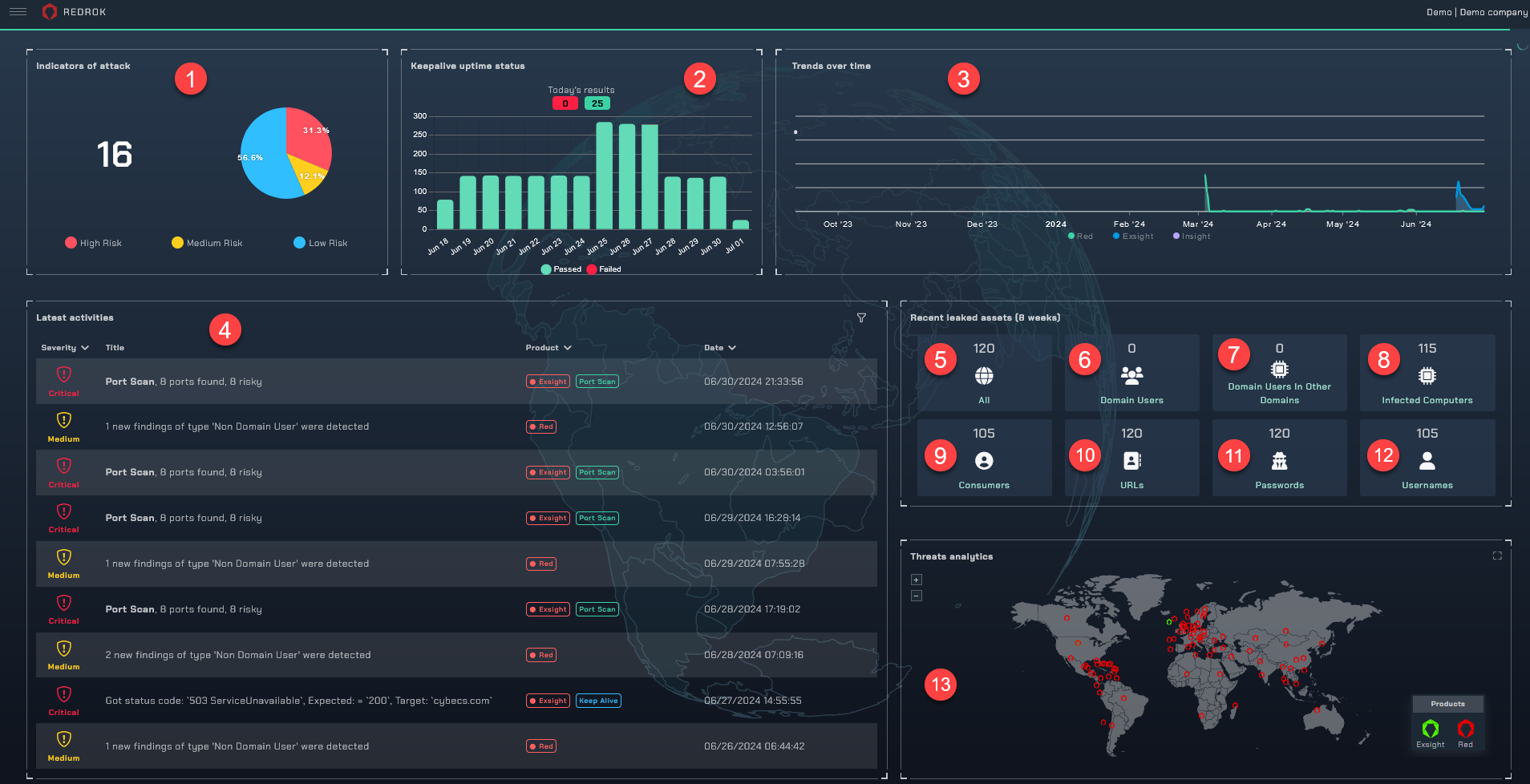
The Indicators of Attack (IoA) feature in RedRok is a powerful tool designed to provide a comprehensive overview of potential security threats. …
This tutorial will guide you through the main features of the interface, ensuring you understand how to navigate and utilize each section …
Securing Active Directory Without Changing Passwords Alone RedRok provides a strategic approach to securing Active Directory (AD), going beyond simple measures such …
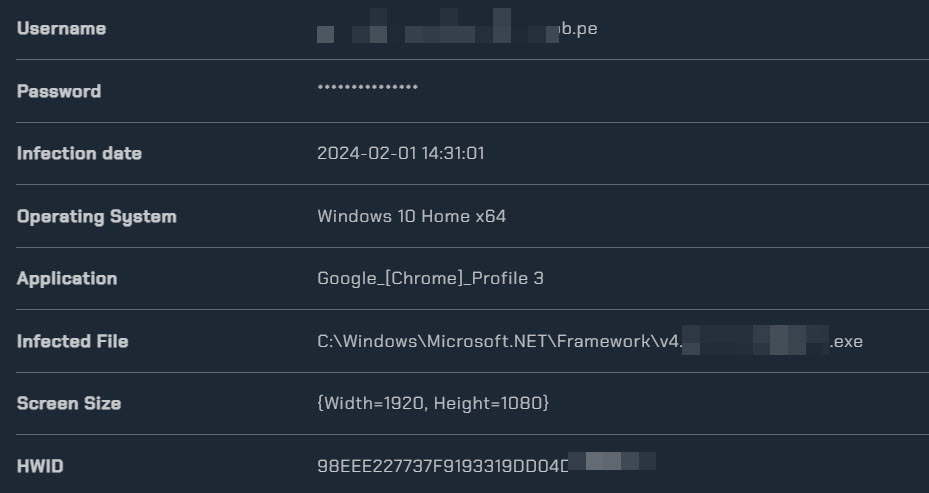
How to Check Your Hardware ID (HWID) on Windows RedRok is designed to help you locate and stop malware—like stealers or keyloggers—on …
We’re thrilled to announce that RedRok will participate in the Gulf Information Security Expo & Conference (GISEC) this year.
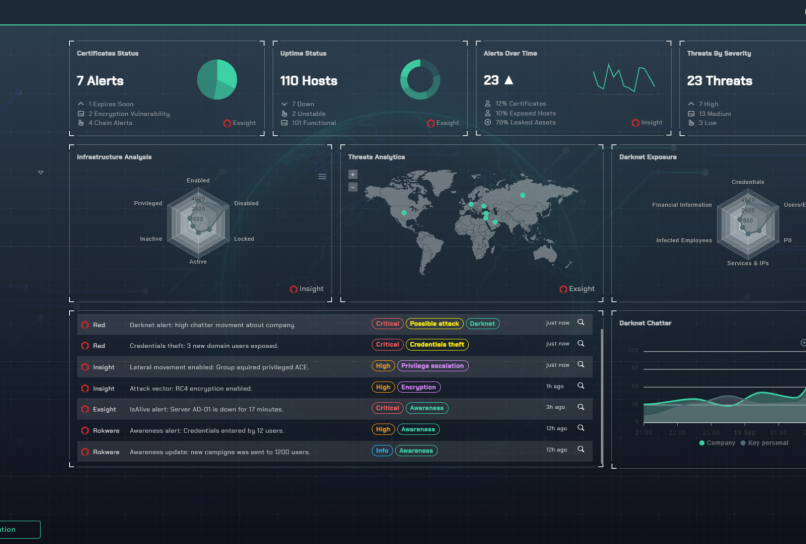
Red monitors the Dark Web for leaks, offering real-time alerts to help you prevent data breaches and counter targeted attacks. RedRok stands …
RedRok Integrated Cybersecurity Solution RedRok delivers a unified cybersecurity solution through the seamless integration of its core modules: Threat Intelligence Services, External …
RedRok Cybersecurity Platform RedRok offers a comprehensive cybersecurity platform designed to provide continuous threat exposure management and proactive defense against evolving cyber …
Resources
Our Platform Documentation